

With increased digitization and networking aboard ships, the risk for data abuse and cybercrime also increases. Anyone considering the possibilities of Maritime 4.0 must also consider the increased requirements for IT security – and more importantly, find suitable solutions for implementing it.
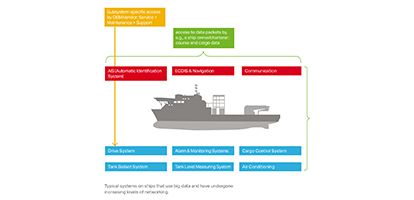
A ship’s various intelligent subsystems ensure problem-free operation: from tank and ballast water management through drive control up to alarm and monitoring systems. They all function using industrial automation technology. At many points, advantages result from networking these subsystems – for example, when ship operations can run with greater resource- or energy efficiency.
The exchange of sensitive data also increases everywhere systems are networked. And yet this is not enough. In comparison to applications on land, ships have additional electronics like navigation, tracking and collision warning systems. They serve the safety of the ship; however, they also represent an additional threat, primarily because they not only increase the level of onboard networking, but also establish external connections. For these connections, Internet-based network technologies or mobile services are seeing increasing use. And these communication paths provide access points for manipulation – particularly at the points between the ship and land.
Access to or the reading of sensitive data is a comparatively less important problem when compared with the effects caused by hackers introducing malware into the control systems of ships or drilling rigs, altering coordinates, or accessing a vessel’s security-relevant subsystems. These acts don’t just endanger IT security, they also impede functional safety, and ultimately the crew’s safety. This is precisely why recommendations regarding IT security have increased along with the level of digitization and networking. The American Bureau of Shipping, the Baltic and International Maritime Council, Lloyd’s Register Group, the UK Chamber of Shipping, and the European Union Agency for Network and Information Society have all published guidelines regarding IT security aboard ships. In general, they define processes, model approaches or technical measures for implementing IT security; for the most part, these align with the guidelines for automation technology.
“IT by design” instead of “defense in depth”
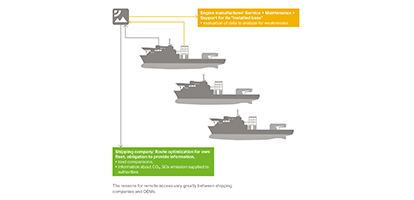
There also seems to be agreement that additional communication relations are generated by Industry 4.0 or Maritime 4.0, providing an increasing potential for cyberattacks. What is more important is that isolation concepts are reaching their limits. This is because of the opportunities provided by networking, which both increases the frequency of outside access and allows much deeper penetration into the ship’s automation systems than before. There is a completely transparent reason for this: by using remote solutions, shipping companies obtain the possibility for remote diagnosis of their ships, which allows them to optimize their fleets and remarket the recorded data. In addition, they can reduce labor costs if fewer personnel or a less qualified crew is used that can receive support from engineers on land for repairs. And finally, better networking of shipping companies and harbor unions improves the logistics at the docks and reduces fuel consumption for the ships. Simply preventing external access cannot be a solution for fixing security on ships. Defense in depth, however, which has previously been considered as state of the art, will soon become insufficient – even if it starts with access limitations, network segmentations and monitoring systems on the various levels of ship automation.
Security concepts are increasingly required that always function, regardless of the time or remote access point. The new demand is for “IT Security by Design,” that is, functions of IT security that are integrated from the start into the configuration of a layer-based security architecture in the controllers.
As Reliable as the Tides
Long, unplanned idle times can be prevented in many situations by using technology with a high level of reliability and fast delivery of replacement parts. Although the business of replacement parts is of interest to BESI – and likewise other OEMs – the Bremen company places a great importance on the international availability of replacement parts. “If a ship owner is stuck somewhere off the coast of Africa and needs an I/O module from us, then every hour counts. If we have to fly to Africa ourselves, then our service-related costs would quickly outstrip profitability.” In this case, it is substantially more logical to use standardized industrial products with a high market penetration, meaning that they can also be purchased on site. “No matter how profitable the replacement part business is, the systems have to start running again fast,” agrees Michael Borchers, Chief Technical Officer at BESI. According to Borchers, the daily charter costs for ships the size of the CSCL Indian Ocean, which has a capacity of 19,000 standard 20-foot long containers, can exeed $40,000.
From the PLC to the cloud – securing the paths that data travels
Such technical possibilities already exist and are capable of closing gaps in security. For example, a reliable means of communication is the establishment of a virtual private network (VPN), based on OpenVPN and using SSL/TLS connections (Secure Sockets Layer, Transport Layer Security). These connections enable the transmission of encrypted data, even over wireless communication systems. WAGO establishes such VPN tunnels using OpenVPN or IPsec directly from the WAGO PFC200 Controller. The WAGO controller additionally records all relevant measurement and control data, encrypts it directly in the controller using SSL encryption and transmits the data as VPN. This means that no additional VPN tunnels have to be established by modems or routers, and, what may be more decisive, the line between the controller and modem is then directly encrypted as well.